The Essentials of 2FA: Securing Your Digital Life
By Jill Berkowitz
- Published: May 13, 2024
If you’ve ever worried about the possibility of someone hacking into your email, online bank account, or social media apps, you’ve likely been relying only on a password, but 2FA, short for Two-Factor Authentication, is one of the most popular ways to protect ourselves and our data. It’s an extra security layer.
Ready to learn how and why to use 2FA?
What is Two-Factor Authentication? MFA vs 2FA
We spend so much time online. Accounts for this, accounts for that. Passwords for this. Passwords for that. Within those accounts are a lot of data that’s tied back to you - it’s important you keep it safe and prevent others from accessing it.
Two-factor authentication is a subset of multi-factor authentication (MFA). OK, but what is MFA? Multi-factor authentication is a fancy way of saying “using more than one factor” to prove it’s really you. 2FA is the most common type of MFA.
- Passwords alone aren’t sufficient. They could be copied, forgotten, lost, or stolen. 2FA keeps things extra safe.
- 2FA adds an extra layer of security. Even if someone gets a hold of your password, they won’t be able to access your account because they don’t have the second factor.
If you receive a One Time Password (OTP verification via SMS) and don’t have any further steps before successfully logging in, the chances are that you are using 2FA. If, after this step, you get asked for your mother’s maiden name, the name of your first pet, or the street you grew up on, you will be using MFA, because it’s requesting additional factors, going beyond the basic 2FA authentication.
Some people use the term Multi-Factor Authentication (MFA) interchangeably with Two-Factor Authentication. Both terms refer to account security that requires more than one verification method to access an account.
2FA for Shared Accounts: Common Security Challenges
Sharing Accounts is a relatively common practice across multiple industries and some examples of this are:
- Shared Inbox for Human Resources
- IT Helpdesk Ticketing System
- Expenses / Invoicing Tracker
What has happened, and still happens, is that someone is trying to access an account. 2FA sends a verification code to one person’s phone - but they’re not with that person. They don’t have access to their phone and can’t log in.
2FA is critical for security, but it can be a real headache when the codes are tied to personal devices.
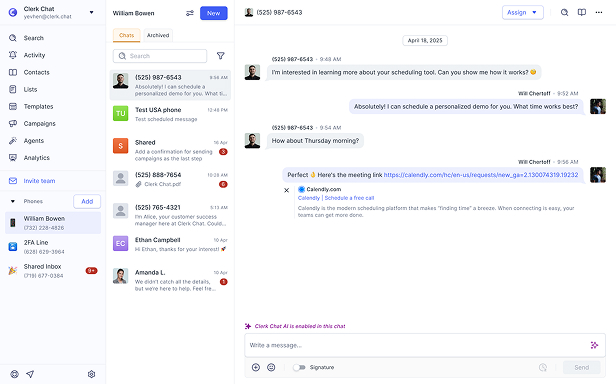
However, SMS marketing services like Clerk Chat help solve the problem. As a company that’s able to help businesses of all sizes whether enterprise needs or SMS for small businesses, 2FA can codes can be sent to a shared phone number inbox. And here’s what happens:
- Your accounts stay protected.
- Everyone who needs access will have it.
Clerk Chat creates a non-VoIP mobile capable number that acts just like a shared line on a mobile device. This number can receive codes from banks, SaaS companies - anywhere, really. The codes flow into a shared inbox that everyone on your team can access.
As a bonus, Clerk Chat also offers multiple SMS integrations with popular software solutions including Microsoft Outlook, Salesforce, and Webex.
By sending the one-time-password via email or a dedicated shared phone number inbox, this solution offers both excellent security and solves the hassles of only one person receiving it. It is also still possible to log which person is attempting to access the account based on their location and computer login. This is a way to enable accountability.
Making Sense of 2FA Security
There has been an upsurge in state-sponsored cyber attacks, and two-factor authentication has become a necessary way of securing corporate and government systems. Here’s why:
- Passwords alone are now unable to adequately protect accounts from hackers as the technology being used to crack passwords is improving all of the time.
- Two-factor authentication makes it much more difficult to access an account without authorization as the code is only sent to the phone number on file for the recipient.
- Since only the last few digits of your number are shown, it makes it harder for someone to guess your phone number and intercept the code in time before it expires.
If you’re feeling concerned about your business security, 2FA helps avoid becoming victim to cyber threats.
How does Two-Factor Authentication Work?
Two-Factor Authentication works by using a non-VoIP number for SMS verification. This just means that it uses an actual phone number, not one that was generated as Voice Over Internet Protocol. A non-fixed VoIP number is one that has been set up virtually rather than assigned to a traditional phone line.
There are two main takeaways here:
- Real phone numbers are more difficult to fake.
- Network providers can properly deliver messages from real numbers.
If you’re setting up 2FA for the first time, use a dedicated mobile number that has been properly vetted for compliance: 10DLC Registration. 10DLC compliance is a set of rules that are used to verify the identity and use case of businesses sending SMS.
This is important because it helps keep your accounts secure. Scammers won’t be able to pretend to use your number to send fake codes, you’ll actually receive codes on time as the number is verified, and you’ll avoid fines.
If you have a number you want to use but it’s not set up to receive codes, you can investigate porting a mobile number, as this allows you to retain the use of your existing number, rather than be assigned a new one. This might be especially useful if you’re responsible for managing someone’s accounts.
Alternatively, if you’re interested in learning more about how to send texts from a different number altogether, there are resources available.
What are the Benefits of Two-Factor Authentication?
Security - Without an additional factor other than a password, someone won’t be able to access your account. By using services that focus on 10DLC compliance and Enterprise SMS, you emphasize security and reliability.
Simplicity - One of the most difficult parts of instituting any new security settings is the difficulty in persuading existing users to adapt how they interact with your system. It can become a source of friction if the verification method is too complex. 2FA is familiar to most, making it less of a hurdle.
Time - It can take time to implement any new system, but with 2FA being so widely used by a variety of internet-based companies, most people will already have come across it and will be well-versed in how to use it by the time you introduce it. There’s less need for training.
Location Independence - Remote work has been on the rise for at least a few years, but with that comes security risks. 2FA adds an extra layer of protection regardless of where your employees are working. It also makes it a bit easier to scale as there’s no need to compromise security.
Trust - People want to know their data is safe. Offering 2FA shows your commitment to customer security.
The Future of 2FA
Two-factor authentication is going to be around for a considerable period of time. It is a simple solution to a difficult problem, making it a popular answer for online security.
As we know, technology continues to develop - but so do cyber threats. 2FA will likely become more sophisticated - and may become just one part of Multi-Factor Authentication, as opposed to one type. Regardless, the core idea of using more than one factor to access an account will remain essential.
Just like a house or building that needs a strong foundation, your business security does, too. Ready to learn more? Explore Clerk Chat’s Security Center.
Jill is a former middle school ELA teacher who has discovered a fascination for content in the B2B tech world. When she isn't writing for Clerk Chat or hosting the 160 Characters podcast, she can be found spending quality time with her husband, three children, and their dog. Follow her journey on LinkedIn.
In this article:
Ready to use your business number for text messaging?
Thousands of businesses are already experiencing the power of conversational messaging through SMS. Join us. Free trial and paid tiers available.
Get Started#Subscribe
Get product updates in your inbox
Tutorials, features, and Clerk Chat news delivered straight to you.