Communication Protocol
[kəˌmjuːnɪˈkeɪʃən ˈproʊtəkɔːl]Communication protocols are standardized rules and formats that govern how messages are transmitted between systems and devices in business messaging. These technical frameworks determine message capabilities, delivery methods, and the entire communication experience between businesses and customers.
Why Communication Protocol Matters
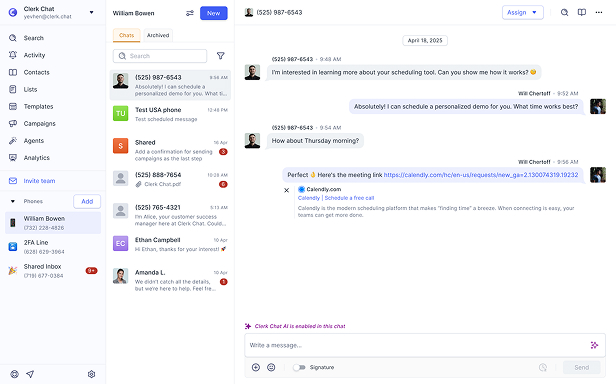
Communication protocols form the invisible infrastructure powering every text message, defining not just technical transmission but the entire user experience. The protocol choice determines whether businesses can send simple text alerts or rich interactive experiences with images, buttons, and real-time responses. This technical decision directly impacts customer engagement, with studies showing 3x higher interaction rates for rich media messages compared to plain text, demonstrating how protocol capabilities translate to business results.
Beyond features, protocols affect fundamental business metrics through their impact on delivery reliability and cost structures. SMS protocols achieve 98% global delivery rates through established carrier networks, while newer protocols like RCS offer advanced features but reach only 15-20% of devices. Protocol selection influences per-message costs by up to 500%, with SMS costing pennies while MMS and RCS can reach dimes per message. Understanding these trade-offs enables businesses to balance functionality needs with budget constraints and audience reach requirements.
The strategic importance of protocols extends to competitive differentiation and regulatory compliance. Businesses leveraging advanced protocols like RCS create branded experiences that stand out in crowded message inboxes, while those relying solely on basic SMS risk appearing outdated. Simultaneously, different protocols offer varying levels of security, delivery confirmation, and audit capabilities essential for regulated industries. Financial services require protocols supporting transaction verification, healthcare needs HIPAA-compliant options, and global businesses must consider regional protocol variations and restrictions.
How Communication Protocol Works
Communication protocols operate through layered technical processes that transform business messages into delivered customer communications:
Message Origination: When businesses send messages, the content first enters the messaging platform where protocol selection occurs. The system analyzes factors including recipient number type, carrier capabilities, message content (text vs multimedia), and regional restrictions to determine optimal protocol usage.
Protocol Encoding: Each protocol uses specific encoding standards. SMS employs GSM 7-bit encoding for basic text or UTF-16 for special characters, limiting messages to 160 or 70 characters respectively. MMS protocols package multimedia content using MIME encoding similar to email. RCS uses modern JSON formatting enabling complex interactive elements.
Network Transport: Different protocols use distinct transport mechanisms. SMS rides on cellular signaling channels originally designed for network control, ensuring delivery without data connections. MMS and RCS require data channels, using HTTP/HTTPS for content delivery. SMPP (Short Message Peer-to-Peer) creates direct connections between messaging platforms and carrier infrastructure.
Carrier Handling: Mobile carriers process messages differently based on protocol. SMS messages queue in carrier SMSCs (Short Message Service Centers) for up to 72 hours attempting delivery. MMS content stores temporarily on carrier MMSCs with notification sent via SMS. RCS messages route through carrier IMS (IP Multimedia Subsystem) infrastructure or Google’s Jibe platform.
Device Reception: Recipient devices must support specific protocols for successful delivery. All mobile phones handle SMS natively, while MMS requires configuration for data access. RCS needs compatible devices and carrier support, with automatic SMS fallback when unavailable. Protocol negotiation happens transparently, selecting the highest mutual capability.
Delivery Confirmation: Protocols provide varying confirmation levels. SMS offers basic delivery reports indicating carrier acceptance. MMS adds download confirmation when recipients retrieve content. RCS provides typing indicators, read receipts, and real-time presence information. Business platforms aggregate these protocol-specific confirmations into unified delivery analytics.
Best Practices with Communication Protocol
Implement Protocol Hierarchy - Establish clear protocol selection logic prioritizing capabilities while ensuring delivery. Start with capability detection for RCS, fall back to MMS for multimedia needs, and default to SMS for guaranteed delivery. Create content adaptation rules that gracefully degrade rich messages for basic protocols while maintaining core message value.
Optimize Content for Each Protocol - Design messages specifically for protocol constraints rather than forcing adaptation. Keep SMS messages under 160 characters to avoid splitting. Compress images for MMS to stay under carrier size limits (typically 300-500KB). Leverage RCS capabilities like suggested reply chips and rich cards when available. Test rendering across protocols before campaign launch.
Monitor Protocol-Specific Metrics - Track performance indicators unique to each protocol. For SMS, monitor segment usage and concatenation success. MMS requires monitoring download rates and content expiration. RCS metrics include interaction rates with rich elements and fallback frequency. Set up alerts for protocol-specific delivery issues requiring investigation.
Plan for Protocol Evolution - Build flexible architecture supporting new protocols without major refactoring. Abstract protocol differences behind unified APIs allowing easy protocol addition. Stay informed about emerging standards like RCS Business Messaging evolution and 5G messaging capabilities. Participate in carrier beta programs for early protocol access.
Ensure Cross-Protocol Consistency - Maintain brand experience across different protocol capabilities. Create visual guidelines adapting logos and colors for various protocol constraints. Develop message templates that convey consistent information whether delivered as rich RCS or plain SMS. Test customer journeys across protocol combinations to identify experience gaps.
Address Security Requirements - Layer additional security atop basic protocol capabilities. Implement application-level encryption for sensitive data regardless of protocol transport security. Use protocol features like RCS sender verification for brand authentication. Maintain detailed logs of protocol usage for compliance auditing and security incident investigation.
Balance Cost and Capability - Develop smart routing rules considering both protocol costs and business value. Reserve expensive protocols like RCS for high-value interactions such as purchase confirmations or support conversations. Use cost-effective SMS for routine notifications. Calculate protocol ROI by comparing engagement improvements against increased costs.
Real world examples
Common misconceptions
Different protocols like SMS, RCS, and SMTP have unique architectures and capabilities
Legacy protocols like SMS remain dominant due to universal compatibility and reliability
Protocols define user experience, feature availability, and business messaging capabilities
Protocol selection significantly impacts delivery rates, speed, and multimedia support
Related terms
In this article:
Ready to use your business number for text messaging?
Thousands of businesses are already experiencing the power of conversational messaging through SMS. Join us. Free trial and paid tiers available.
Get StartedFAQ
Have questions? We've got answers.
Find what you need quickly and clearly with our most frequently asked questions.
A communication protocol is a standardized set of rules defining how messages are formatted, transmitted, and received between systems. In business messaging, protocols like SMS (Short Message Service), MMS (Multimedia Messaging Service), and RCS (Rich Communication Services) determine message capabilities, delivery methods, and feature availability. These protocols establish everything from character limits and multimedia support to delivery confirmations and encryption standards, forming the technical foundation for all business-customer text communications.
Protocol selection depends on your messaging requirements, target audience, and technical infrastructure. SMS protocols offer universal reach with 160-character limits, ideal for alerts and simple notifications. MMS protocols enable image and media sharing for marketing campaigns. RCS protocols provide app-like experiences with rich media and interactive elements but limited device support. Consider SMPP for high-volume needs or HTTP/REST APIs for web integration. Evaluate factors including delivery reliability, cost per message, feature requirements, and recipient device compatibility.
Protocol implementation costs vary significantly based on complexity and volume. SMS protocols typically cost $0.01-0.05 per message with minimal setup fees. MMS protocols cost 3-5x more than SMS due to media handling. RCS implementation requires $5,000-50,000 initial investment plus $0.02-0.10 per message. SMPP connections for high-volume sending involve $500-2,000 monthly fees but reduce per-message costs by 40-60%. HTTP API integrations usually require 20-40 development hours plus ongoing per-message charges. Infrastructure costs include servers, bandwidth, and compliance certifications.
RCS protocols offer significant advantages over SMS, including rich media support, typing indicators, read receipts, and 8,000-character limits versus SMS's 160 characters. RCS enables branded messaging with company logos and verified sender information. However, SMS protocols maintain superiority in universal device support (98% vs 15% for RCS), reliability across all networks, and consistent delivery without data connection requirements. SMS also offers lower costs and simpler implementation. Many businesses use hybrid approaches, defaulting to RCS when available and falling back to SMS.
Security varies dramatically across messaging protocols. Traditional SMS uses no end-to-end encryption, making it vulnerable to interception, though carrier networks provide basic transport security. RCS implements client-to-server encryption but not full end-to-end encryption. SMPP connections support TLS encryption for message transport between servers. For sensitive communications, businesses must implement application-level encryption regardless of protocol. Consider protocols supporting delivery confirmations and audit trails for compliance. Healthcare and financial services often require additional security layers beyond standard protocol encryption.
Optimize protocol usage by implementing intelligent routing that selects protocols based on recipient capabilities and message content. Use capability detection to identify RCS-enabled devices before defaulting to SMS. Implement protocol-specific optimizations: compress images for MMS, use concatenation efficiently for long SMS, and leverage RCS suggested replies. Monitor protocol-specific metrics including delivery rates, latency, and error codes. Set up redundancy with multiple protocol options and automatic failover. Batch similar protocol messages for efficiency. Regular testing across different carriers and devices ensures optimal protocol performance.